Bitcoin: A Comprehensive Introduction

Introduction
Recently Bitcoin has been creating a storm not only in communities across the web, but also in legislative bodies across the world. It has the potential to do to online payments what Napster did to music, and it’s a fascinating topic. Many bits have featured in the media over the consequences of the currency, but there exists surprisingly little knowledge even amongst the members of the tech-savvy Generation-Y of how the paperless monetary system actually works. This crypto-currency is a quasi-anonymous distributed electronic monetary system that ignores national borders, banks and economic doctrines. With those buzzwords well and truly outed, it’s time to understand how it all works.
The solution Bitcoin provides is elegant but complicated, and each part of the protocol that creates a potential problem is solved by an elegant solution. Is this a digital currency for a digital age, or is the conventional currency that we’ve trusted for thousands of years a tried and tested method that we should be happy to continue with? In this series of articles, we will talk about how this digital currency works from the technical and ethical points of view.
How much of your shopping, online or otherwise, involves paper and metal money? For most people, a sizeable proportion of purchases is made with debit and credit cards, either in shops or over the web. In these instances, the existence of paper money is implied by your bank, who will transfer the appropriate money electronically to the supplier of the goods you are purchasing. What is really happening ‘under the hood’ is that the bank subtracts from their own record of your account’s balance the amount you’ve paid, and adds it onto the balance of the account owned by the supplier (of course, in reality, we use different banks, so banks must send information of the transactions between themselves).
Most of you might see a benefit to having some form of digital currency. With paper money becoming less and less relevant, why not get rid of it completely and represent money solely as electronic entities? This is what Bitcoin and other digital currencies try to do, but before we go into detail about how Bitcoin actually works, it is essential to first understand the ramifications of some reasonably simple mathematics. This kind of maths is important to the security of every web user, so it’s very relevant in the Internet Age.
The word ‘crypto-currency’, often used in conjunction with Bitcoin, alludes to the use of cryptography. Bitcoin itself is actually just what is known as a ‘protocol’. In the computing science sense, a protocol is a method by which two (or more) parties exchange something, using a shared set of instructions. For instance, I am using the ‘English language’ protocol to communicate with you. In currency protocols like Bitcoin, cryptography is used to help protect the identity of individuals, while at the same time verifying that particular users are who they say they are. This might sound paradoxical but it relies on technology that is ubiquitous on the World Wide Web today. Any time that you’ve ever shopped on a secure website, your browser has, created on your behalf, an encrypted connection between you and the company using very strong techniques.
The really cool aspect of this type of encryption is that it doesn’t require you and the company to agree a password. Instead, through a process based on what is known as Diffie-Hellman Key Exchange 1, two keys (what you and I might call passwords) are produced that can respectively encrypt and decrypt the information. The clever part of the process is that the keys themselves never need to be exchanged between you and the company, even before you start using them, so there is minimal possibility of eavesdropping. Of course, there are vulnerabilities elsewhere in such systems, usually involving the squishy meatbags using them, but in terms of agreeing on a secure, common communication mechanism between the two parties, this works a treat. The security of the system is based on the special properties of prime numbers 2. Encryption using this type of agreement is known as public key encryption because one of the keys can be safely published in the open without compromising the other, and the technology has been a standard member of the security arsenal throughout the history of the World Wide Web. With sufficiently long and complex keys, it is in theory completely secure.
Another concept fundamental to Bitcoin is the use of hashing. The process of hashing involves taking a piece of information of any length – be it a password, a record of a transaction or an entire book – and producing a string of essentially random characters of fixed length, based on that information. Hashing algorithms make use of a member of the mathematical toolbox called a one-way function. One-way functions are sets of mathematical instructions which allow an output to be easily calculated for any given input, but are extremely difficult to perform in reverse (in effect, the function can only be calculated in one direction). This is a bit like when you mix paints. It’s easy enough to work out the colour that paints mixed together will produce, but it’s difficult to take some already mixed paint and work out which particular colours were used, especially if many different colours are used. With hashing functions, the length of the input is a bit like the number of paints used to make the final colour. A suitably designed one-way function will be sufficiently complex, such that the only way to work out the answer would be to obtain the output by brute force, which is to say, to try every possible input to the function until its output matches the hash. This method is extremely time-consuming, even for the world’s fastest supercomputers, and for a sufficiently long hash it is completely impossible to brute force the answer within a human’s lifetime. The foundations of the security of Bitcoin and the World Wide Web are based on the difficulty of this task.
Crowbarring the paint metaphor once more into this article, a demonstration of Diffie-Hellman Key Exchange can be seen in Figure 1.
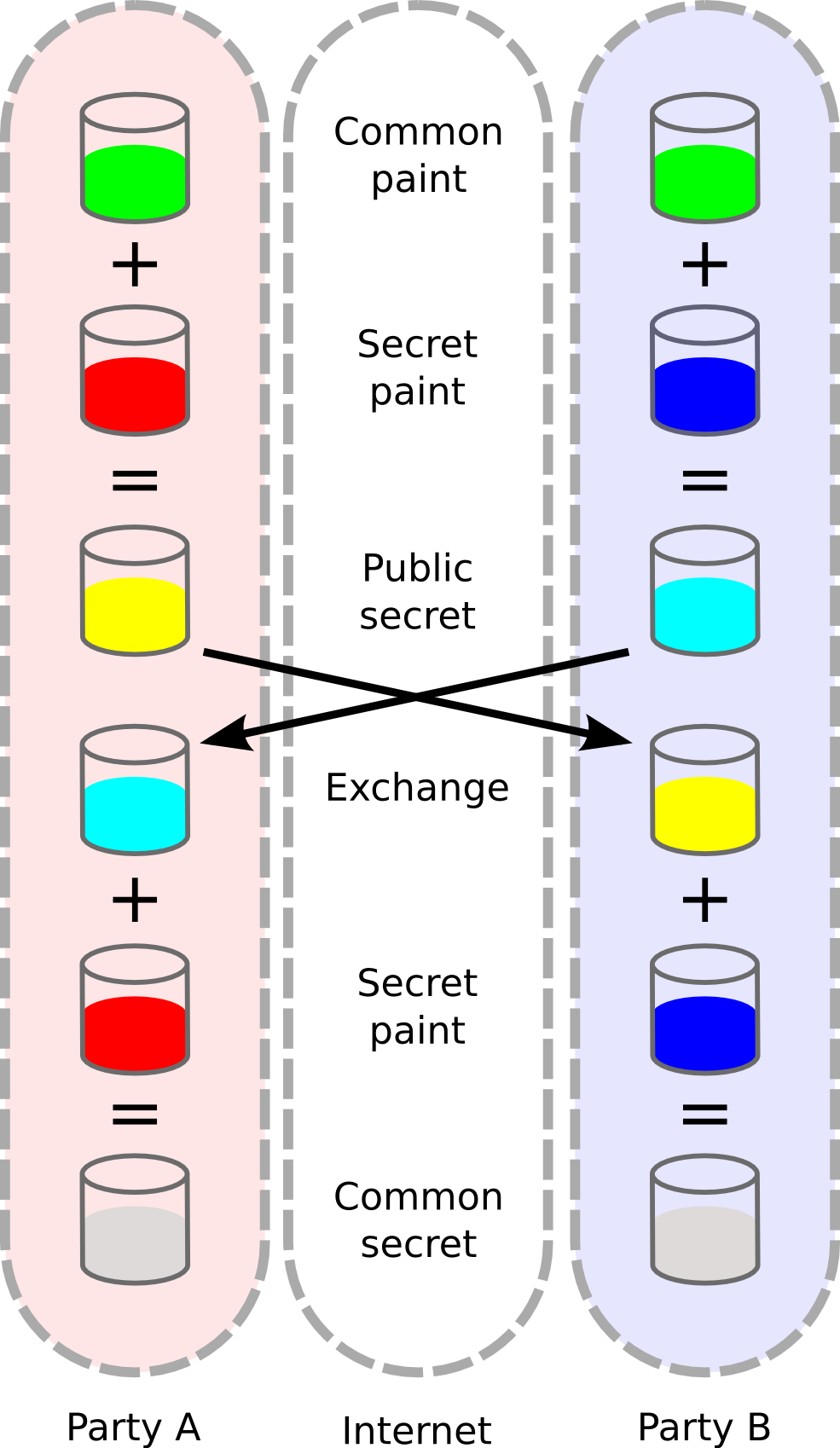
Figure 1: Diffie-Hellman Key Exchange with paints. To decide on a common paint (key) to use, two parties can first start with their own private paint colour. Adding this to a predetermined shared paint colour, they can then exchange paints. Each user then adds their own secret paint to the other’s mixture, producing a common paint colour. This takes place without the common or the private paint colours being exchanged across open channels at any point, so it is immune to this traditional form of snooping. The difficulty of taking a mixed paint and working out the colours that made it is analogous to the difficulty of taking a hash and working out what the data used to make the hash was.
Hashing functions are often used by website owners to store passwords. Instead of storing a user’s real password, they store the hash of that password. When logging in, the website simply compares the hash of whatever you enter in the password field to the hash they already have in their database. If the website’s database were ever to be compromised, then only the hashes of the website’s users would become visible, and not their actual passwords. Owing to a hash function’s difficulty to invert, it would be extremely difficult for the attacker to then obtain real passwords. The use of hashes allows a website owner to verify that a particular piece of information has been provided (such as a password) without having to store the information itself, only its hash. This is a crucial abstraction also utilised by Bitcoin to help to anonymise its users. Furthermore, Bitcoin uses the properties of hash functions to cut down on the size of the data that users must store on their computers and to perform a task known as ‘mining’ — more on this in later articles.
The combination of two widespread web technologies in public key encryption and hash functions helps to allow the Bitcoin protocol to verify that an owner of some bitcoins is the genuine owner of those bitcoins. The public key encryption aspect lets a user verify their identity as the one possessing the bitcoins without actually having to reveal their real identity. Without vast amounts of luck and computing power, only the owner of the private key could possibly know the public key which will unlock a transaction, so by publishing this public key, a user is verifying their ownership. That is not the end of the story, however. There are many issues that digital currencies face due to their electronic nature. In the next article, we will discuss how Bitcoin attempts to overcome these issues.
Go to Part 2











